Biometric
Biometrics are physical or behavioral characteristics unique to an individual, such as a finger or palm print, iris pattern or face image. Because each individual has unique biometric data, solutions based on biometrics offer a better and more accurate means of ensuring program integrity. By matching patterns of individuals against databases of records, our customers are better able to protect and secure citizens from crime and theft made possible by fraudulent identities. Though Id cards and passwords serve as excellent safeguards, but they are not immaculate in terms of safety and can be tampered and falsified.
3TS Technologies’s Capabality in Biometrics:
3TS Technologies has turnkey solutions for virtually any environment. At 3TS Technologies we integrate tightly with databases containing records to optimize the speed and accuracy of matches.
We use the most advanced and the best of authentication and identification systems in the field of biometrics which includes the following:
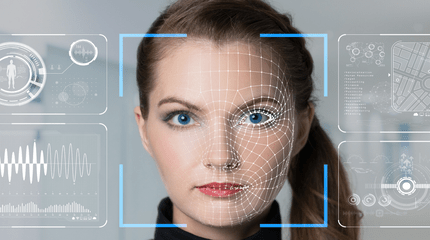
Facial Recognition
In addition to taking video footage, surveillance cameras ,capture the overall facial structure, including the distance between eyes, nose, mouth and jaw edge. This image is instantly analyzed and compared to database records. A user usually stands within two feet of the camera and most of the time is required to perform some human facial movement, like smiling or ‘ blinking to prevent the use of a mold or fake face. The decision is typically made in less than 5 seconds.

Retina Scan
Retinal scanning analyzes the very unique layer of blood vessels at the back of the eye. Scanning uses a low-intensity tight source and an optical coupler. A person is required to keep his head still, look closely in the device and focus on a green light while scanning is performed. The white process takes lo-ls seconds. Since there is no known way to reproduce a retina, and one from a dead person would weaken too seoon, no additional precautions are taken to prevent faking a living human. There is no need to remove glasses.

Iris Recognition
Another method of eye recognition is iris-analysis of more than zoo points in the colored tissue surrounding the pupil. In this case user can be either close to the video camera or 2 feet away, depending on the device. Iris recognition does not use infrared light beams, so it is safer to an eye. The identification is done in less than s seconds and may use tight shone to watch for pupil dilation to prevent users from fooling the system. There is no need to remove glasses.

Voice Recognition
People speak a pass phrase into a microphone to validate their identities. Another revet of security can be added by requiring a user to reproduce low and high sound frequencies. Both validation procedures typically take less than five seconds.

Vascular Recognition
Face or hand vein thickness and their locations are considered unique enough to identify a person. An infrared scan from a curved reader device performs a vascular scanning process and then compares it to the database records to find a match.

Hand Geometry
As a user places a hand on a metal plate, the system takes more than go measurements of the length, width, thickness and surface of the hand – and fingers. It is a simple, fast and accurate procedure. The drawback is that this scan is unable to tell the difference between a living, fake or dead hand, if pressure is property applied. For optimum security, it is best to combine hand geometry with another method authentication process.

Fingerprint
A user gently places fingers against a small reader device. Characteristics such as whorls, arches, and loops are recorded along with-the patterns of ridges. furrows, and minutiae. Depending on the security level in the organization, fingerprinting may require a match of six or seven identical points, while law enforcement agencies may prefer a match of twelve or more.
 Leekee i2i Business Solutions Private Limited
Leekee i2i Business Solutions Private Limited